Application Autotuning and Autonomic Computing
A large class of applications expose several software-knobs that alter extra-functional properties of the elaboration ( e.g. execution time or resource usage) and of the output (e.g. size of the result or its accuracy). A change on the configuration of those knobs, may lead to drastic changes in the value of the properties of interest for the end user. In fact, application requirements involve several properties that are usually in contrast with each others. For example, in the context of a video surveillance scenario, the end-user would like to minimize the energy consumption, given a constraint on a minimum level of quality of the output and a lower bound on the frame per second processed by the application. While in the context of an HPC application, the end-user would like to maximize the quality of results, with a constraint on the time to solution, for a given input set.
Since the extra-functional properties depends on the underlying architecture and on the evolution of the system, finding a one-fits-all configuration is not a trivial task. For instance, the resources allocated to the application might change due to workload fluctuation or the application might be heavily input- dependent. Moreover, the application requirements might change at runtime to respond to external stimuli. For instance, while the surveillance system described in the previous example detects a threat, the application requirement might ignore the energy consumption of the application.
In the context of autonomic computing, this group aims at enhancing an application with a dynamic adaptation layer, to provide self-optimization capabilities, according to application requirements and to the available resources.
Professor:
PhD students:
- Davide Gadioli
- Emanuele Vitali
- E. Paone et al. Evaluating orthogonality between application auto-tuning and run-time resource management for adaptive opencl applications. Application-specific Systems, Architectures and Processors (ASAP), 2014 IEEE 25th International Conference on. IEEE, 2014
- D. Gadioli, G. Palermo, C. Silvano. Application autotuning to support runtime adaptivity in multicore architectures. Embedded Computer Systems: Architectures, Modeling, and Simulation (SAMOS), 2015 International Conference on. IEEE, 2015
- C. Silvano et al. The ANTAREX approach to autotuning and adaptivity for energy efficient HPC systems. Proceedings of the ACM International Conference on Computing Frontiers. ACM, 2016
- A. H. Ashouri et al. Cobayn: Compiler autotuning framework using bayesian networks. ACM Transactions on Architecture and Code Optimization (TACO) 13.2 (2016): 21
- J. Martinovic et al. DSL and Autotuning Tools for Code Optimisation on HPC Inspired by Navigation Use Case. Supercomputing, 2016
Compiler Technology
A compiler is a computer program or a set of computer programs that translates code written in a source language to a target language. The source language is typically a human-readable programming language while the target language is usually a lower-level language, directly executable by a machine.
While it is typically desirable that the output code be semantically equivalent to the source code, it is possible to insert other code to realize additional, extra-functional properties, without altering the functional goals of the original program.
While it is typically desirable that the output code be semantically equivalent to the source code, it is possible to insert other code to realize additional, extra-functional properties, without altering the functional goals of the original program.
The members of the compiler technology sub-group work in particular on the following areas:
- Compiler technology for security: the group designs and implement compiler extensions able to analyze the source code (typically, the implementation of a cryptographic primitive) to check whether it is leaking information that should remain secret via a side channel, such as power emissions. If this is the case, the compiler modifies the code to increase the resilience against this kind of vulnerability.
- Compiler support to emerging architectures: the group realizes optimized back-ends for the LLVM compiler targeting novel architectures and explores possible optimizations for the architectures.
- Compilers and runtime libraries for parallel programming models: the group develops compilers and runtime libraries to allow programs written with the target parallel programming language and/or application programming interface can be run on a specific architecture, targeting in particular heterogeneous architectures.
- Reverse-engineering: this is the newest research area (in the past the group has worked on dynamic compilation (2002-2009)). The main aim is to statically translate machine language into the intermediate representation used by the compiler, which can then be compiled to a different machine language (binary-to-binary translation, used to port code for which the source is lost or cannot be obtained), to the same machine language (after modifying the code, e.g. to provide instrumentation for profiling or securization), or to a human-readable programming language (for reverse engineering and analysis).
Professors:
PhD Students:
- Stefano Cherubin
- Alessandro Di Federico
- Anna Pupykina
- G. Agosta, A. Barenghi, G. Pelosi, M. Scandale. The MEET Approach: Securing Cryptographic Embedded Software against Side Channel Attacks. In IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, volume PP, issue 99
- S. Campanoni, G. Agosta, S. Crespi Reghizzi, A. Di Biagio. A highly flexible, parallel virtual machine: design and experience of ILDJIT. In Software: Practice and Experience, Volume 40 Issue 2, pages 177-207, 2010
- A. Di Federico, M. Payer, G. Agosta. rev.ng: a unified binary analysis framework to recover CFGs and function boundaries. In Proceedings of the 26th International Conference on Compiler Construction (CC 2017). ACM, New York, NY, USA, 131-141, 2017
- M. Gautschi et al. Tailoring instruction-set extensions for an ultra-low power tightly-coupled cluster of OpenRISC cores. IFIP/IEEE International Conference on Very Large Scale Integration (VLSI-SoC), Daejeon, pp. 25-30, 2015
- A. Di Federico, G. Agosta. A jump-target identification method for multi-architecture static binary translation. In Proceedings of the International Conference on Compilers, Architectures and Synthesis for Embedded Systems (CASES '16). ACM, New York, NY, USA, , Article 17 , 10 pages, 2016
Postgraduate course:
Computer Architecture

The computer architecture research area describes the rules and techniques to organize and implement the functionality of a computing system. In our group, we focus on the design of methodologies and architectures for current and future multi-cores, ranging from embedded to high performance processors. In particular, the research activities are organized in three different branches:
- Energy-Performance Optimization of the Uncore in Multi-cores: the research of the group in this area aims at designing and implementing novel coherence protocols, cache hierarchy as well as on-chip interconnects for new generations of multi-cores
- Designing Secure Computer Architectures: the research group focuses on the design and implementation of novel architecture design strategies for both embedded CPUs and cryptographic hardware accelerators to face the so-called side-channel attacks (new security threats that exploit the possibility to correlate the physical information extracted form the device with the actual data-dependent computation in order to extract the secret key)
- Design and Implementation of Power Efficient Embedded Multi-Cores: the research group aims at the design and verification of novel RISC-based microarchitectures for the embedded market segment with a twofold objective. First, explore different microarchitectural solutions for low-power scenarios. Second, provide FPGA-based prototypes to advance the hardware-software co-design for resource allocation and low-power aspects
Professors:
Research Fellow:
- D. Zoni et al. BlackOut: Enabling fine-grained power gating of buffers in Network-on-Chip routers. Journal of Parallel and Distributed Computing, 2017
- D. Zoni, J. Flich, W. Fornaciari. CUTBUF: Buffer Management and Router Design for Traffic Mixing in VNET-Based NoCs. IEEE Transactions on Parallel and Distributed Systems, 2016
- D. Zoni, F. Terraneo, W. Fornaciari. A DVFS Cycle Accurate Simulation Framework with Asynchronous NoC Design for Power-Performance Optimizations. Journal of Signal Processing Systems, 2016
- D. Zoni, F. Terraneo, W. Fornaciari. A control-based methodology for power-performance optimization in NoCs exploiting DVFS. Journal of Systems Architecture, 2015
- D. Zoni and W. Fornaciari. Modeling DVFS and Power-Gating Actuators for Cycle-Accurate NoC-Based Simulators. ACM Journal on Emerging Technologies in Computing Systems, 2015
Bachelor courses:
Postgraduate course:
Runtime Resource Management
The end of Dennard’s scaling has been one of the most disruptive events occurring in the evolution of the computing platforms. In order to cope with the subsequent increase in chips power density, hardware designers have progressively moved towards solutions that leverage the concepts of parallelism and heterogeneity. As a consequence, modern architectures feature an increasing number of shared computational resources that are power-hungry, can possibly be different in nature, and can be concurrently used by multiple applications.
This increasing hardware complexity has in turn affected the software stack: task scheduling and mapping have become challenging problems due to the need of maximizing the performance of applications while minimizing power, temperature and contention on the shared resources.
The activities of the run-time resource management sub-group aims at addressing the aforementioned problems, considering system scenarios that span from embedded and mobile systems to High-Performance Computing (HPC) infrastructures. Part of the research outcomes are then exploited for the development of the Barbeque Run-Time Resource Manager (Barbeque Open-Source Project ).
Guaranteeing a suitable system utilization without causing problems that could compromise the system itself is paramount. This is the ultimate goal of the run-time resource management group, which, in order to get the best results, can always count on the close collaboration with all the other groups, which have competences in both hardware and software management.
The activities of the run-time resource management sub-group aims at addressing the aforementioned problems, considering system scenarios that span from embedded and mobile systems to High-Performance Computing (HPC) infrastructures. Part of the research outcomes are then exploited for the development of the Barbeque Run-Time Resource Manager (Barbeque Open-Source Project ).
Guaranteeing a suitable system utilization without causing problems that could compromise the system itself is paramount. This is the ultimate goal of the run-time resource management group, which, in order to get the best results, can always count on the close collaboration with all the other groups, which have competences in both hardware and software management.
Professors:
Research Fellow:
PhD Students:
- Domenico Iezzi
- Anna Pupykina
- Federico Reghenzani
- Michele Zanella
- P. Bellasi, G. Massari, W. Fornaciari. A RTRM proposal for multi/many-core platforms and reconfigurable applications. 7th International Workshop on Reconfigurable and Communication-Centric Systems-on-Chip (ReCoSoC), York, pp. 1-8, 2012
- P. Bellasi, G. Massari, W. Fornaciari. Effective Runtime Resource Management Using Linux Control Groups with the BarbequeRTRM Framework. ACM Trans. Embed. Comput. Syst. 14, 2, Article 39 (March 2015), 17 pages, 2015
- G. Massari et al. Extending a Run-time Resource Management framework to support OpenCL and Heterogeneous Systems. In Proceedings of Workshop on Parallel Programming and Run-Time Management Techniques for Many-core Architectures and Design Tools and Architectures for Multicore Embedded Computing Platforms (PARMA-DITAM '14). ACM, New York, USA, Pages 21 , 6 pages, 2014
- G. Massari et al. Combining application adaptivity and system-wide Resource Management on multi-core platforms. International Conference on Embedded Computer Systems: Architectures, Modeling, and Simulation (SAMOS XIV), Agios Konstantinos, pp. 26-33, 2014
- S. Libutti, G. Massari, W. Fornaciari. Co-scheduling tasks on multi-core heterogeneous systems: An energy-aware perspective. In IET Computers & Digital Techniques, vol. 10, no. 2, pp. 77-84, 3, 2016
Postgraduate courses:
Security – Cryptography

Cryptography is the science that provides technical solutions to ensure that a message, sent or stored, has the following properties:
- Confidentiality: the message is not intelligible to whoever is not authorized to read it
- Integrity: the message is not modified without the author’s consent
- Authenticity: the origin of the message can be traced back to a specific author
In particular, the security group focuses on the following areas of research:
- Efficient software and hardware implementation: Providing highly efficient implementations is crucial in devices working with limited energy supply and that are, therefore, tightly constrained by the available energy pool (e.g. mobile phones, small sensors, embedded medical devices). The interests of the security group focus on exploiting architectural features avaliable on mobile and low power devices to provide effective and efficient implementations. In particular, the group is currently tackling techniques for efficient realizations of innovative cryptosystems, such as quantum-computer resistant cryptographic primitives and lightweight symmetric ciphers for constrained devices.
- Side channel attacks and countermeasures: A quite effective way to extract the secret encryption key from a physical cipher implementation is to observe one or more side-effects of the computation itself (e.g. the time required to compute a certain primitive, the energy consumed in doing so). This approach to the extraction of the secret key is known as a side channel attack, and is able to breach standard abiding and functionally correct implementations regardless of the mathematical security of the implemented primitive. With respect to these attacks, the group designed automated compiler-based securization techniques to detect vulnerabilities and protect cryptographic primitives against side channel attacks. The implementation of such analysis and automated protection was realized within the popular LLVM compiler framework.
- Cryptography in emerging application domains: Cyber-physical security: the group designed a key agreement protocol and an overlay encryption protocol for the KNX standard, which is used for building automation in households, hotels, hospitals. The designed protocol enciphers and authenticates the data sent without modifying the datagram headers, allowing a drop-in deployment of the protected devices.
- Data security and privacy: The group tackled the security and privacy of large amount of encrypted outsourced data when dealing with an honest-but-curious storage provider. They also designed an efficient solution to protect the access pattern to remotely stored data, with in-house equivalent privacy guarantees.
- Social network privacy and security: The overall aim of the research has been to shift the handling of security-related aspects onto the client. In particular, the group designed a social network platform where the client handles the encryption and decryption of the messages, and is the only one in knowledge of the encryption keys, an approach known as end-to-end encryption. The group is currently working on the design of an asynchronous messaging protocol providing private acquaintances discovery with respect to the service provider.
- Secure e-mail communication and data authentication: The group reviewed the security of the well-established GPG secure e-mail and data authentication protocol highlighting unnoticed weaknesses and proposing mitigations.
Current project:
Professors:
PhD students:
- Alessandro Di Federico
- Nicholas Mainardi
- G Agosta, A Barenghi, G Pelosi. A code morphing methodology to automate power analysis countermeasures. Proceedings of the 49th Annual Design Automation Conference, 77-82, 2012
- AD Biagio, A Barenghi, G Agosta, G Pelosi. Design of a parallel AES for graphics hardware using the CUDA framework. Parallel & Distributed Processing. IPDPS 2009
- G Agosta, A Barenghi, M Maggi, G Pelosi. Compiler-based side channel vulnerability analysis and optimized countermeasures application. DAC, 81:1-81:6, 2013
- A Barenghi, M Beretta, A Di Federico, G Pelosi. A privacy-preserving encrypted OSN with stateless server interaction: The Snake design. Computers & Security 63, 67-84, 2016
- A Barenghi, GM Bertoni, L Breveglieri, G Pelosi, S Sanfilippo, R Susella. A fault-based secret key retrieval method for ECDSA: analysis and countermeasure. ACM Journal on Emerging Technologies in Computing Systems (JETC), 13 (1), 8, 2016
Postgraduate course:
Thermal Management
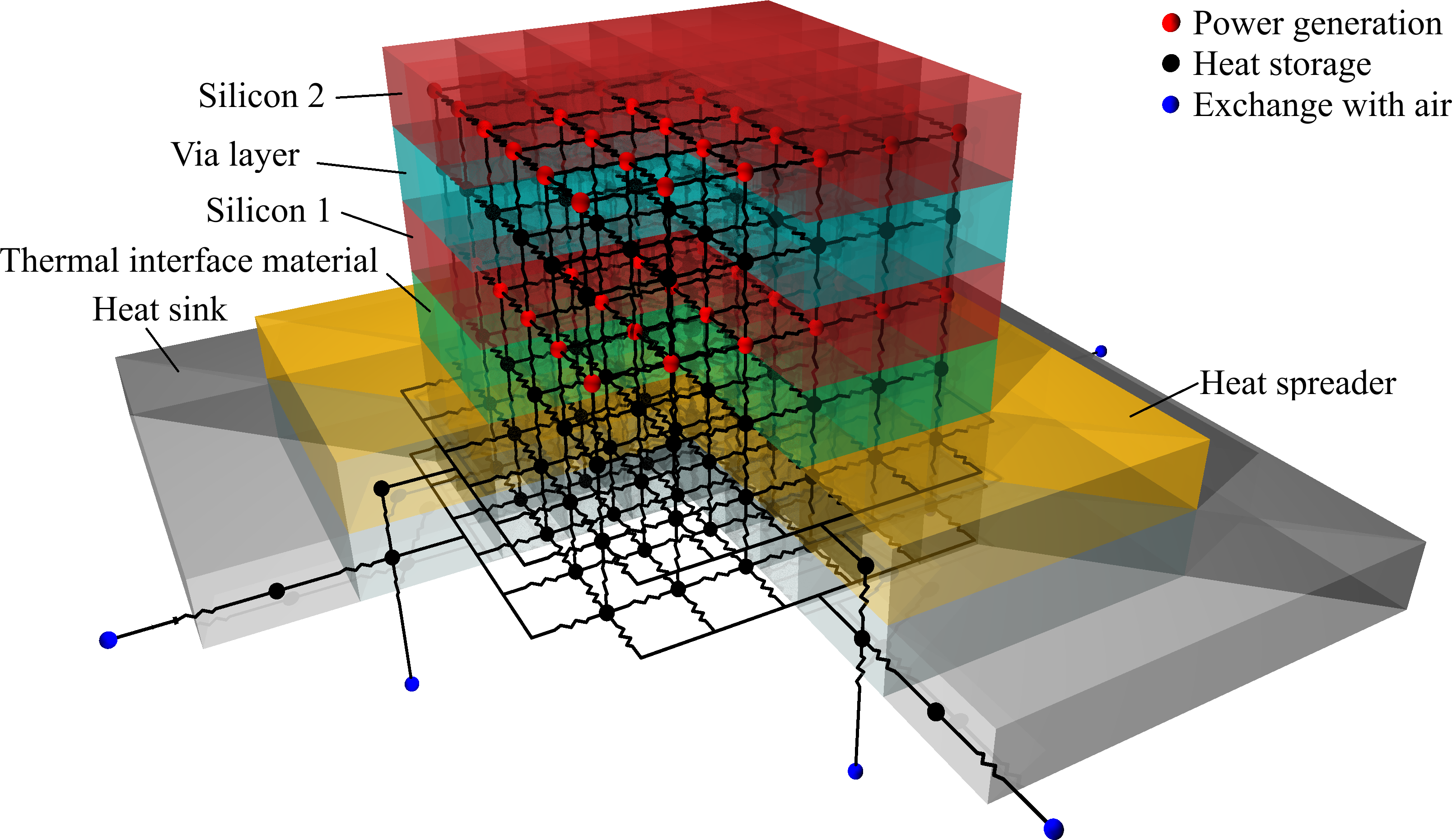
The development of increasingly powerful CPUs goes hand in hand with the search for new dissipation technologies able to prevent the onset of high-temperature related problems. In this context, the group works on both hardware and software solutions:
- (hardware) Heatsinks design: Through measurement experiments and simulations, the group’s work aims at finding new dissipation technologies able to keep the temperature of new generations of CPUs under control. These are indeed characterised by higher level of parallelism and performance, features that necessarily lead to a higher power dissipation
- (software) Dynamic Thermal Management: An efficient Thermal Management strategy needs also to process software mediums that can intervene whenever the heatsink activity is not sufficient. The group’s main target consists in implementing effective Dynamic Thermal Management software policies, able to balance the computing activities, thus keeping the CPU temperature within a certain threshold
Professors:
Research Fellow:
- Dr Federico Terraneo
- A. Leva, F. Terraneo, S. Seva. Periodic event-based control with past measurements transmission. IEEE International Conference on Event-Based Control, Communication, and Signal Processing (EBCCSP), Madeira, Portugal, 2017
- A. Leva, F. Terraneo, I. Giacomello, W. Fornaciari. Event-based power/performance-aware thermal management for high-density microprocessors. IEEE Transactions on Control Systems Technology, 2017
- A. Leva, F. Terraneo, S. Seva, I. Giacomello. High-speed thermal management for power-dense microprocessors. IEEE Conference on Decision and Control (CDC), Las Vegas, USA, 2016
- A. Leva, F. Terraneo, W. Fornaciari. Event-based thermal control for high-density processors. IEEE International Conference on Event-Based Control, Communication, and Signal Processing (EBCCSP), pp.1-8, Krakov, Poland, 2015
- F. Terraneo, D. Zoni, W. Fornaciari. An accurate simulation framework for thermal explorations and optimizations. 7th Workshop on Rapid Simulation and Performance Evaluation: Methods and Tools (RAPIDO'15), pp. 1-6, Amsterdam, The Netherlands, 2015
Wireless Sensor Network
The development of wireless sensor networks has a great potential not only for customers (see IOT), but also and more importantly for the industry and the environment, especially for monitoring purposes. In this context, two features of the devices connected wirelessly are crucial. These are respectively:
- Time synchronization: In order to meet application requirements as well as guarantee an efficient interconnection among all the devices, these must be perfectly synchronised. This way, data get transmitted correctly and don’t get lost, and data fusion from the individual nodes is facilitated. In this context, the group is developing time synchronization systems that take into account both the local clock nonidealities, such as time-varying skew, and network-related issues, such as propagation delays.
- Hardware-Software codesign: the group is developing a WSN platform combining power efficiency, high performance and ease of programmability. The Miosix embedded operating system raises the programming abstraction allowing microcontroller applications to be written in C++11 in a preemptive multitasking environment. The WandStem WSN node provides a time-deterministic platform with hardware-assisted packet timestamping and power consumption introspection capabilities.
Professors:
Research Fellow:
- Dr Federico Terraneo
- F. Terraneo et al. FLOPSYNC-QACS: Quantization-Aware Clock Synchronization for Wireless Sensor Networks. IEEE International Workshop on Real-Time Computing and Distributed systems in Emerging Applications (REACTION), Porto, Portugal, 2016
- F. Terraneo, A. Leva, W. Fornaciari. Demo: A High-Performance, Energy-Efficient Node for a Wide Range of WSN Applications. International Conference on Embedded Wireless Systems and Networks (EWSN), Graz, Austria, 2016
- F. Terraneo et al. Reverse Flooding: exploiting radio interference for efficient propagation delay compensation in WSN clock synchronization. IEEE Real-Time Systems Symposium (RTSS), San Antonio, Texas, 2015
- F. Terraneo et al. FLOPSYNC-2: efficient monotonic clock synchronisation. IEEE Real-Time System Symposium (RTSS), pp. 11-20, Rome, Italy, 2014
- A. Leva, F. Terraneo. Low power synchronisation in wireless sensor networks via simple feedback controllers: the FLOPSYNC scheme. American Control Conference, pp. 5017-5022, Washington DC, 2013
Postgraduate course:
